.NET Samples
The FoxIDs .NET samples show:
- User login and logout with OpenID Connect 1.0 and SAML 2.0
- Client credential grant with secret and certificate
- API calls secured with OAuth 2.0
- Token exchange from access token to access token and SAML 2.0 to access token
Find the sample source in the FoxIDs.Samples repository.
The samples are pre-configured in the FoxIDs online test tenant test-corp and can immediately run locally in Visual Studio on the pre-configured localhost ports.
Take a look at the FoxIDs test configuration in FoxIDs Control: https://control.foxids.com/test-corp
Get read access with the userreader@foxids.comand passwordgEh#V6kSw
You can alternatively configure the samples in your one FoxIDs environment.
Sample index
ASP.NET Core - OpenID Connect - application registration
- AspNetCoreOidcAuthCodeAllUpPartiesSample (online) ← Good starting point!
- AspNetCoreOidcAuthorizationCodeSample
- AspNetCoreOidcImplicitSample
ASP.NET Core - SAML 2.0 - application registration
Blazor - OpenID Connect - application registration
Console app - OAuth 2.0 Client credential grant - application registration
ASP.NET Core API - OAuth 2.0 - application registration
ASP.NET Core - OpenID Connect - authentication method
ASP.NET Core - SAML 2.0 - authentication method
ASP.NET Core - External APIs
Console app - FoxIDs Control API
You can use the JWT tool and SAML 2.0 tool to decode tokens and create self-signed certificates with the certificate tool.
Sample applications
The samples show different applications which trust FoxIDs as an IdP.
AspNetCoreOidcAuthCodeAllUpPartiesSample
Sample (code link) application showing user login and logout with OpenID Connect (OIDC) using authorization code flow as a service provider and requesting login by all authentication methods.
You can test this sample online.
This sample is a good starting point!
The possible authentication methods is configured in the application registration as allowed authentication methods. There can be configured one to many allowed authentication methods. All the configured authentication methods is selected with a star instead of an authentication method name.
Support login/logout with FoxIDs login page, Identity Server, SAML 2.0 IdP sample and all other authentication methods.
API calls:
- Show how to call the API1 sample secured with an access token.
- Show how to call the API1 sample secured with an access token which again call API2 sample using token exchange insight API1.
- Show how to obtained an access token by token exchange, the client use client authentication method client_secret_post. And then call the API2 sample secured with the obtained access token.
Local development domain and port: https://localhost:44349
AspNetCoreOidcAuthorizationCodeSample
Sample (code link) application showing user login and logout with OpenID Connect (OIDC) using authorization code flow as a service provider.
Support login/logout with FoxIDs login page, Identity Server, SAML 2.0 IdP sample and if configured AD FS using SAML 2.0.
Show how to call the API1 sample secured with an access token.
Local development domain and port: https://localhost:44340
AspNetCoreOidcImplicitSample
Sample (code link) application showing user login and logout with OpenID Connect (OIDC) using implicit flow as a service provider.
Support login/logout with FoxIDs login page, Identity Server, SAML 2.0 IdP sample and if configured AD FS using SAML 2.0.
Local development domain and port: https://localhost:44341
AspNetCoreSamlSample
Sample (code link) application showing user login and logout with SAML 2.0 as a relying party.
Support login/logout with FoxIDs login page, Identity Server, SAML 2.0 IdP sample and if configured AD FS using SAML 2.0.
Show how to obtained an access token from an SAML 2.0 bearer token with token exchange, the client use client authentication method private_key_jwt (certificate). And then call the API1 sample secured with the obtained access token.
Local development domain and port: https://localhost:44343
NetCoreClientCredentialGrantConsoleSample
Sample (code link) console application (backend) showing client authentication with OAuth 2.0 Client Credentials Grant using a secret (client authentication method client_secret_post).
Show how to call the API1 sample and API with two IdPs sample secured with an access token.
NetCoreClientCredentialGrantAssertionConsoleSample
Sample (code link) console application (backend) showing client authentication with OAuth 2.0 Client Credentials Grant using a certificate (client authentication method private_key_jwt).
Show how to call the API1 sample and API with two IdPs sample secured with an access token.
NetFramework4.7ClientCredentialGrantAssertionConsoleSample
Sample (code link) .NET Framework 4.7 console application (backend) showing client authentication with OAuth 2.0 Client Credentials Grant using a certificate (client authentication method private_key_jwt).
Show how to call the API1 sample and API with two IdPs sample secured with an access token.
BlazorBFFAspNetCoreOidcSample
Sample (code link client and server) application showing user login and logout with OpenID Connect (OIDC) using authorization code flow in a Blazor BFF (Backend For Frontend) application with a ASP.NET Core backend.
In a BFF architecture the backend handles OIDC, the tokens are never shared with the Blazor client. Instead a session based on an identity cookie secure the application after successfully user authentication.
The sample show how to call the API1 sample from both the Blazor client through a backend API proxy which add the access token to the outgoing API call.
Local development domain and port: https://localhost:44348
BlazorOidcPkceSample
Blazor sample (code link) application showing user login and logout with OpenID Connect (OIDC) using authorization code flow and PKCE as a service provider.
Show how to call the API1 sample secured with an access token.
Local development domain and port: https://localhost:44345
BlazorServerOidcSample
Blazor server sample (code link) application showing user login and logout with OpenID Connect (OIDC) using authorization code flow as a service provider.
Show how to call the API1 sample secured with an access token.
Local development domain and port: https://localhost:44347
AspNetCoreApi1Sample
Sample (code link) API showing how to secure an API with an access token and how to restrict access by scopes.
You can call this sample online.
The API calls API2 sample secured with an access token obtained by token exchange where the client use client authentication method private_key_jwt (certificate).
Local development domain and port: https://localhost:44344
AspNetCoreApi2Sample
Sample (code link) API showing how to secure an API with an access token and how to restrict access by a scope.
You can call this sample online.
Local development domain and port: https://localhost:44351
AspNetCoreApiOAuthTwoIdPsSample
Sample (code link) API showing how to create an API which can accept access tokens from two different IdPs. Each IdP - API relation can be configured with individual resource IDs and scopes.
This scenario occurs most often in a transitional period moving from one IdP to another IdP. Having APIs with dual IdP support the clients can be moved from one IdP to another IdP independent of the APIs.
The sample API can be called by changing comment out code in the NetCoreClientCredentialGrantConsoleSample or NetCoreClientCredentialGrantAssertionConsoleSample samples.
Local development domain and port: https://localhost:44350
Authentication methods samples
The authentication methods samples show different IdPs connected to FoxIDs, where FoxIDs trust the IdP samples.
AspNetCoreSamlIdPSample
Sample (code link) application implementing a SAML 2.0 identity provider (IdP) connected as a SAML 2.0 authentication method in FoxIDs. The sample also show how to do IdP-Initiated login.
You can test this sample online.
Local development domain and port: https://localhost:44342
IdentityServerOidcOpSample
Identity Server (code link) implementing OpenID Connect (OIDC) exposing a OpenID Provider (OP) / identity provider (IdP) connected as a OpenID Connect authentication method in FoxIDs.
Local development domain and port: https://localhost:44346
ExternalLoginApiSample
Sample (code link) application implementing an external login API which is connected as a external login authentication method in FoxIDs.
Local development domain and port: https://localhost:44352
ExternalClaimsApiSample
Sample (code link) application implementing an external claims API which can be configured and called from a claims transform. The external claims API can then add external claims to the issued claims.
Local development domain and port: https://localhost:44353
ExternalExtendedUiApiSample
Sample (code link) application implementing an external extended UI API which can be configured and called to validate dynamic UI elements and optionally return additional claims.
Local development domain and port: https://localhost:44354
ExternalPasswordApiSample
Sample (code link) application implementing an external password API which is connected as an external password API in a FoxIDs environment.
Local development domain and port: https://localhost:44355
FoxIDsControlApiSample
Sample (code link) console application showing how to call FoxIDs Control API.
Configure samples in FoxIDs environment
The samples can be configured in a FoxIDs environment with the sample seed tool or manually through the FoxIDs Control Client.
The sample seed tool is found in the sample solution: tools/SampleSeedTool.
Configure the sample seed tool
The sample seed tool is configured in the
appsettings.jsonfile.
Add the FoxIDs and FoxIDs Control API endpoints to the sample seed tool configuration. They can be added by updating the instance names https://foxids.com and https://control.foxids.com/api. If you are running FoxIDs locally in Visual Studio the endpoints is configured to FoxIDs localhost https://localhost:44330/ and FoxIDs Control API localhost https://localhost:44331/.
"SeedSettings": {
"FoxIDsEndpoint": "https://foxids.com",
"FoxIDsConsolApiEndpoint": "https://control.foxids.com/api"
}
Access to create the sample configuration in a environment is granted in the
masterenvironment. The sample configuration should not be added to themasterenvironment.
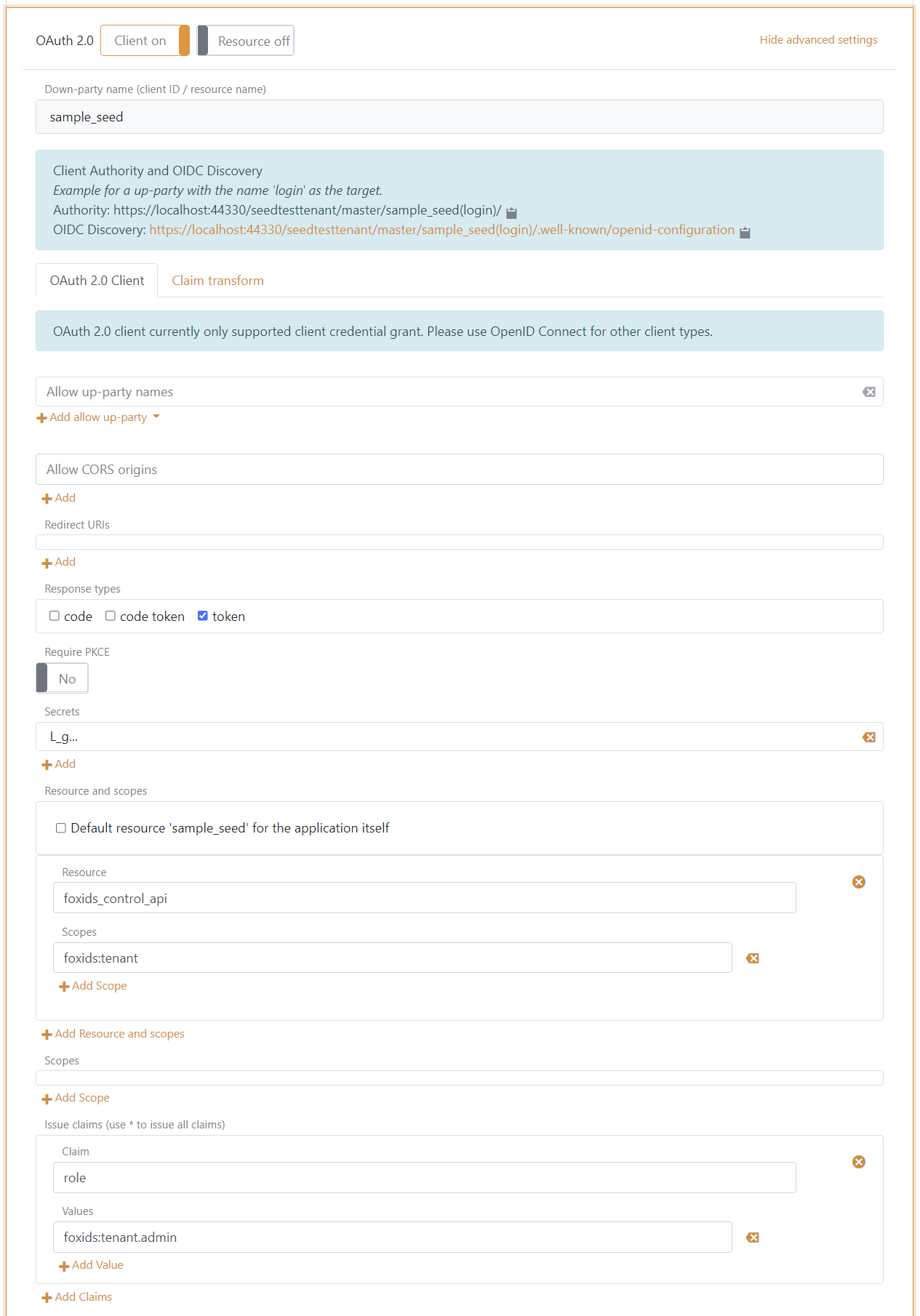
Create a sample seed tool OAuth 2.0 client in the FoxIDs Control Client:
- Select the
masterenvironment and create a OAuth 2.0 application registration, clickOAuth 2.0 - Client Credentials Grant. - Set the client id to
sample_seed. - Remember the client secret.
- In the resource and scopes section. Grant the sample seed client access to the FoxIDs Control API resource
foxids_control_apiwith the scopefoxids:tenant. - Click show advanced.
- In the issue claims section. Add a claim with the name
roleand the valuefoxids:tenant.admin. This will granted the client the administrator role.
The sample seed tool client is thereby granted access to update to the tenant.
Create a new FoxIDs environment for the sample applications or select an existing environment.
Change the tenant, the environment and the sample seed tool client secret in the sample seed tool configured.
"SeedSettings": {
"Tenant": "xxx",
"Track": "xxx",
"DownParty": "sample_seed",
"ClientSecret": "xxx"
}
Change the tenant and the environment configuration for all the samples.
Run the sample seed tool
Run the sample seed tool executable SampleSeedTool.exe or run the seed tool directly from Visual Studio.
- Click 'c' to create the sample configuration
- Click 'd' to delete the sample configuration
The sample seed tool will create and delete configurations for all samples.
The sample applications require a login authentication method with the name login (handles user login). It is created by the sample seed tool if it do not exists. The login authentication method is not deleted if the sample configuration is deleted.