Login, Home Realm Discovery and MFA
FoxIDs handle user login in the login authentication method. There can be configured a number of login authentication methods per environment with different configurations and look and feel.
A environment contains one user repository and all login authentication methods configured in a environment authenticate users with the same user repository.
When a user authenticates, the user's session is associated with the login authentication method. Therefore, a user can authenticate in multiple configured login authentication methods and have multiple separate user sessions.
A user session is not established in the login authentication method if the session lifetime is set to 0 seconds.
A OpenID Connect application registration or SAML 2.0 application registration can authenticate users by selecting an login authentication method.
The login authentication method authenticates users in a two-step login UI with the username and password input on two separate pages.
Home Realm Discovery (HRD)
When you create a application registration it is most often the best solution to use the default star notation (*) to select all the authentication methods.
If a application registration is configured to only be allowed to use one authentication method the user is immediately redirected to that particular authentication method.
If more than one authentication method is allowed the user is redirected to a login authentication method which make it possible to select an authentication method either by client IP address, email domains or regular expressions.
The login UI is not shown if an authentication method is selected based the client IP address.
Client IP address
Select the authentication method based on the client device's / PCs IP address.
Select by IP address or with an IP range:
192.168.0.0/255.255.255.0selects from '192.168.0.0' to '192.168.0.255'192.168.10.0/24selects from '192.168.10.0' to '192.168.10.255'192.168.0.10 - 192.168.10.20selects from '192.168.0.10' to '192.168.10.20'192.168.10.10-20selects from '192.168.10.10' to '192.168.10.20'fe80::/10select e.g. 'fe80::d503:4ee:3882:c586%3'
Email domain
Select the authentication method based on the users email domain.
Select by domains or use (*) to select all domains not configured on another authentication method.
Regular expression
Select the authentication method based on case-insensitive regular expression match of the users email, phone and username.
Select by regular expression:
xyz$match emails and usernames ending with 'xyz'^+45match phone numbers starting with phone code '+45'abdmatch emails and usernames containing 'abc'^q10.*@@xyz\.com$match emails starting with 'q10' at the domain 'xyz.com'
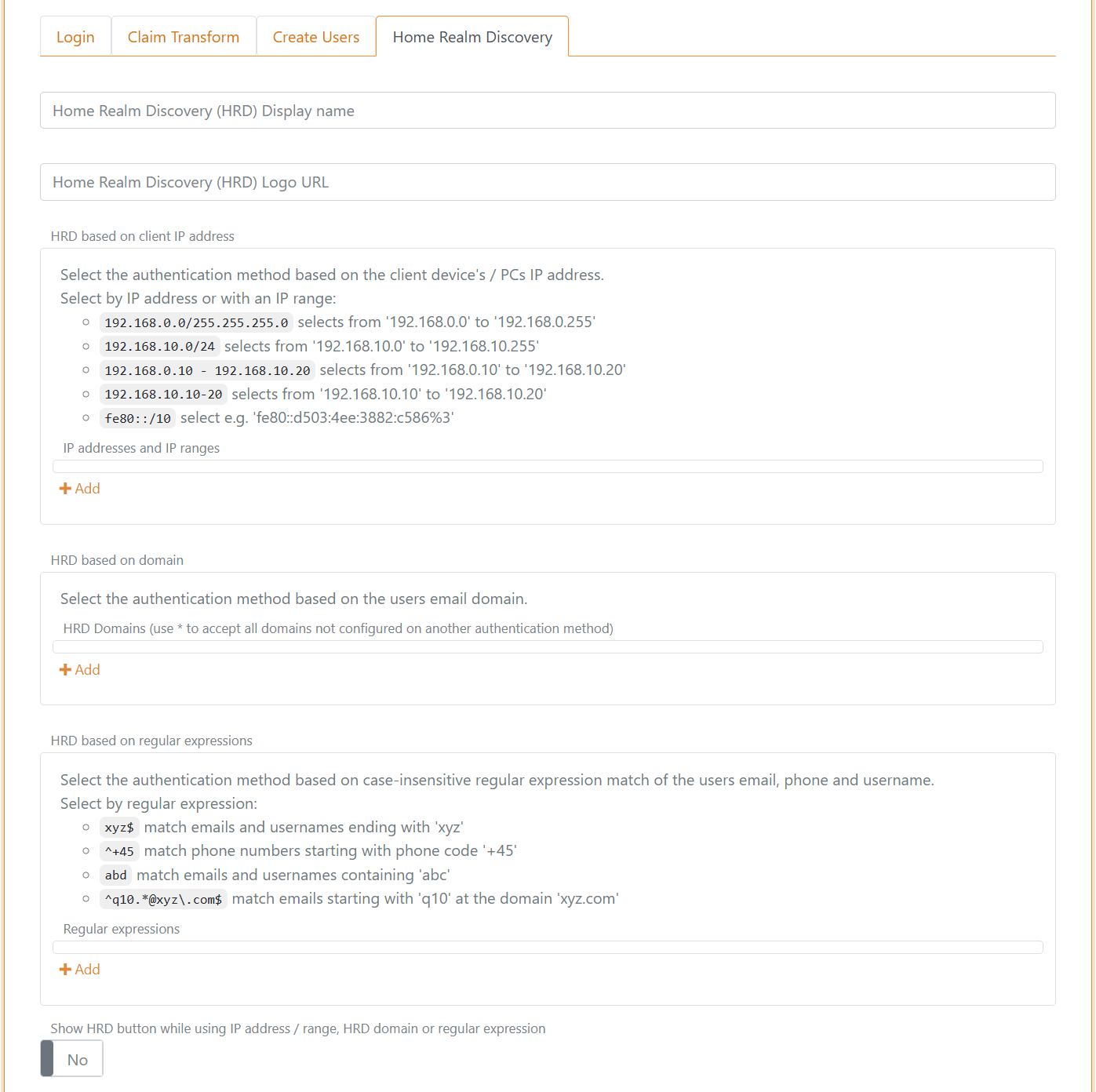
It can be selected if the HRD button should be displayed for the authentication method even if IP address / range, HRD domain or regular expression is configured.
An example of how a login screen with HRD looks like, it can be customised.
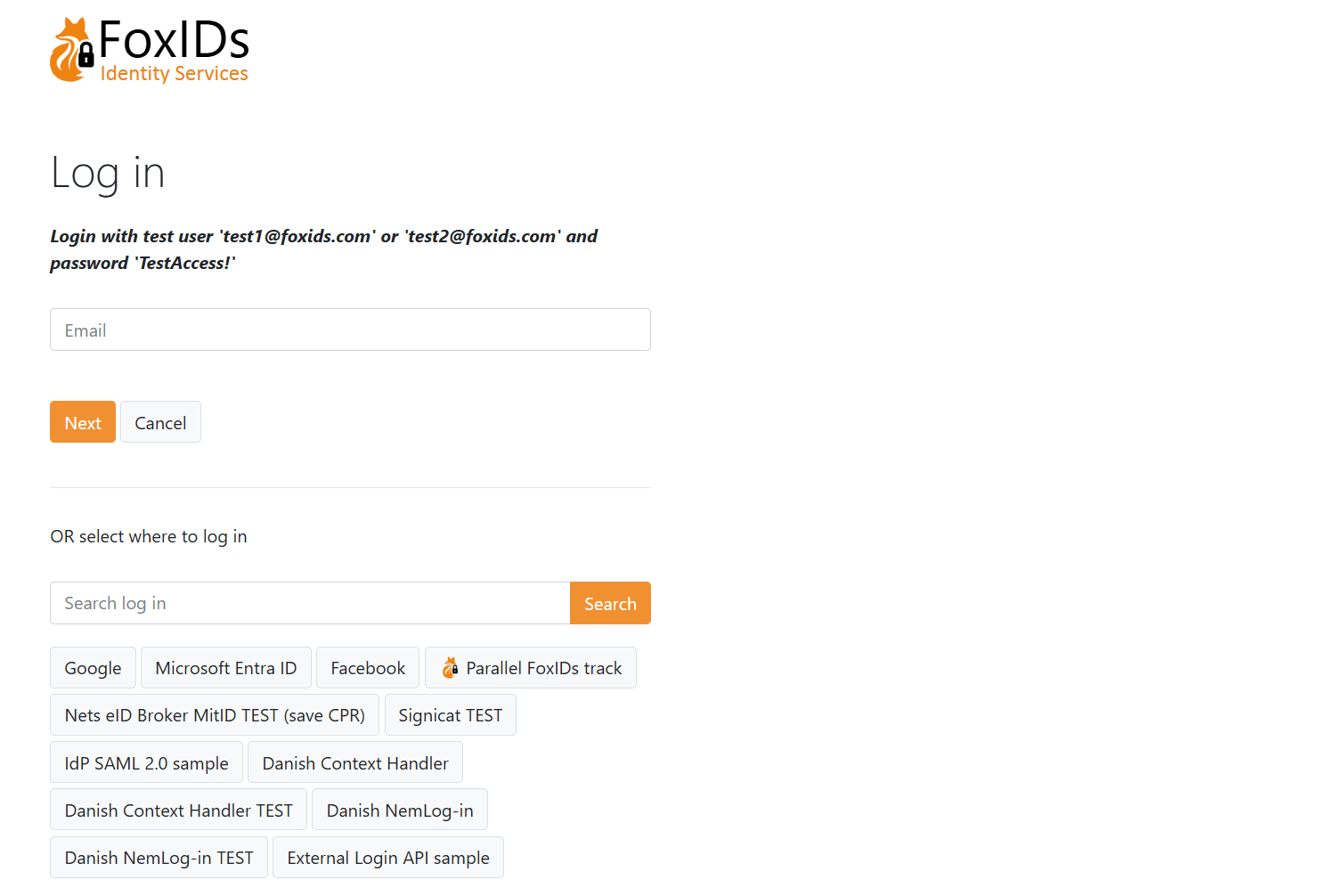
The title, icon and CSS configured on the first allowed login authentication method on the application registration is used. Without an allowed login authentication method configured the title, icon and CSS from the default login authentication method is used.
Two-factor authentication (2FA/MFA)
A login authentication method support two-factor authentication (2FA) / multi-factor authentication (MFA) with an authenticator app, SMS and email.
Two-factor authentication with an authenticator app, SMS and email is per default enabled and is initiated if required.
Two-factor authentication can be set as a requirement in each login authentication method, per user or required by the calling OpenID Connect or SAML 2.0 application registration.
You can use a two-factor authenticator app of your choice like Anthy, Google Authenticator, Microsoft Authenticator and others.
In this example the user is asked to do two-factor authentication with an authenticator app or change to use SMS or email.
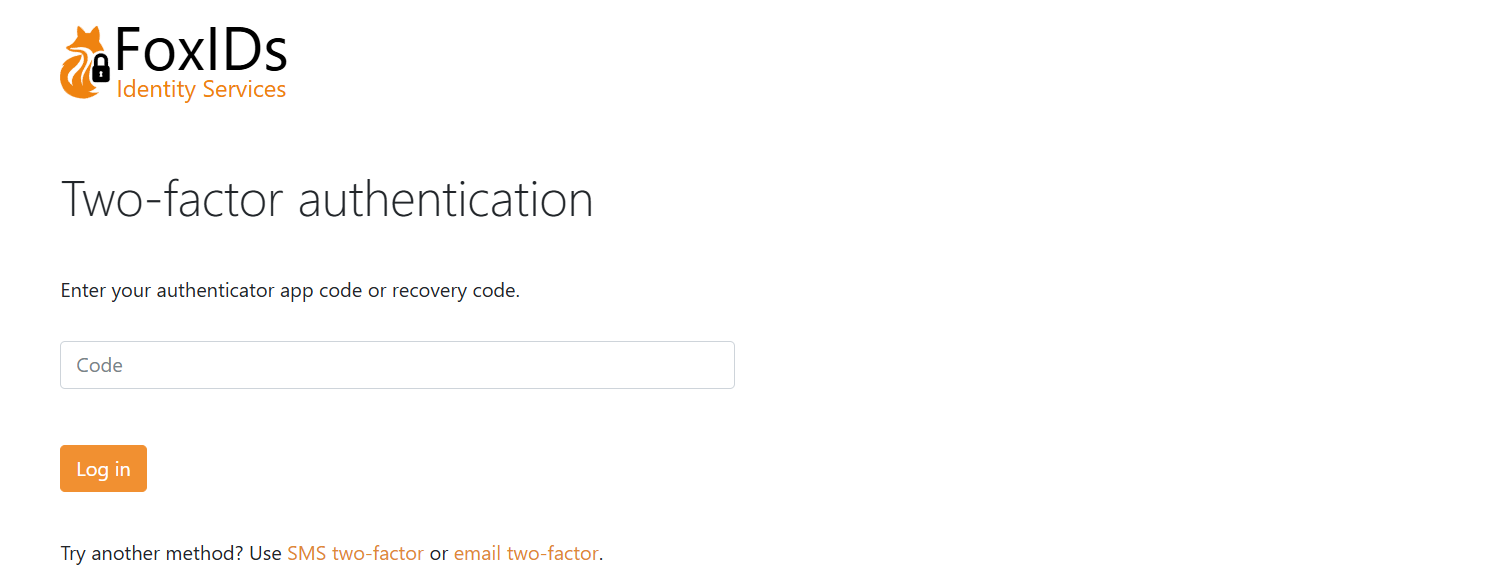
A phone number and email can either be configured as a user identifier or as a claim with the phone_number and email claim types.
The two-factor authentication type is selected as shown in this table.
| SMS two-factor enabled and user has phone number | Email two-factor enabled and user has email | User has registered authenticator app | Possible two-factor type(s) | Selected two-factor type |
|---|---|---|---|---|
| false | false | false | Authenticator app | Authenticator app |
| false | false | true | Authenticator app | Authenticator app |
| true | false | false | SMS - can register authenticator app after SMS verification | SMS |
| true | false | true | SMS and authenticator app | Authenticator app |
| false | true | false | Email - can register authenticator app after email verification | |
| false | true | true | Email and authenticator app | Authenticator app |
| true | true | false | SMS and mail - can register authenticator app after SMS/email verification | SMS |
| true | true | true | SMS, email and authenticator app | Authenticator app |
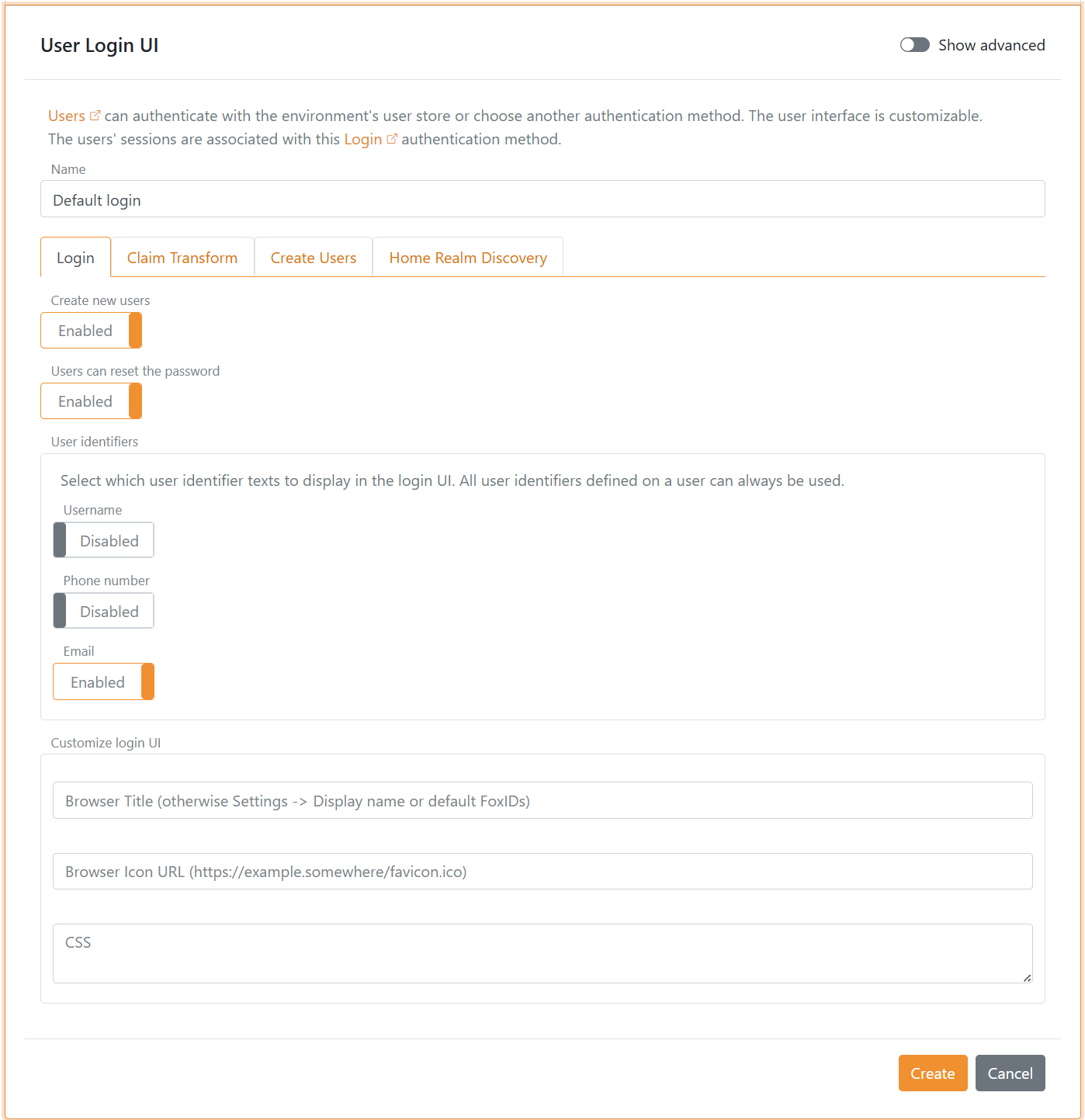
Login configuration
A default login authentication method is created in each environment.
The default login with the name
logincan be changed but not deleted, be careful as you may lose access.
The title, icon and CSS configured on the default login authentication method is use in the case where no login authentication method is selected e.g., on the error page or during HRD selection without a login authentication method.
Configure login options
It can be configured whether users should be allowed to set there password, whether users are allowed to create a new user online, which user identifiers to use and if the user should login with a password or one-time password (OTP) via email or SMS.
The UI can be customised and much more.
New users can be created by the administrator through the Control Client or be provisioned through the Control API.
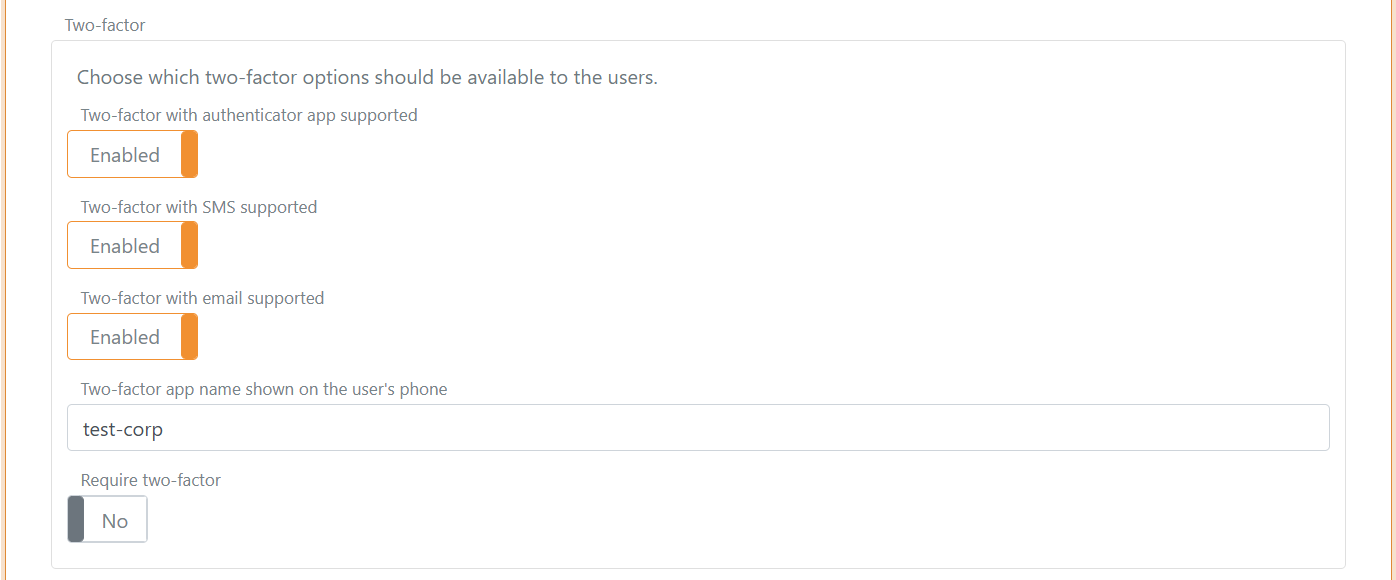
Configure two-factor authentication (2FA)
The two-factor options can be changed and the authenticator app name shown for the user's can be changed. The name is per default set to the tenant's name. You most likely want to change the name to something more human readable.
You can select to require two-factor authentication for all users authenticating using the login authentication method.
Configure user session
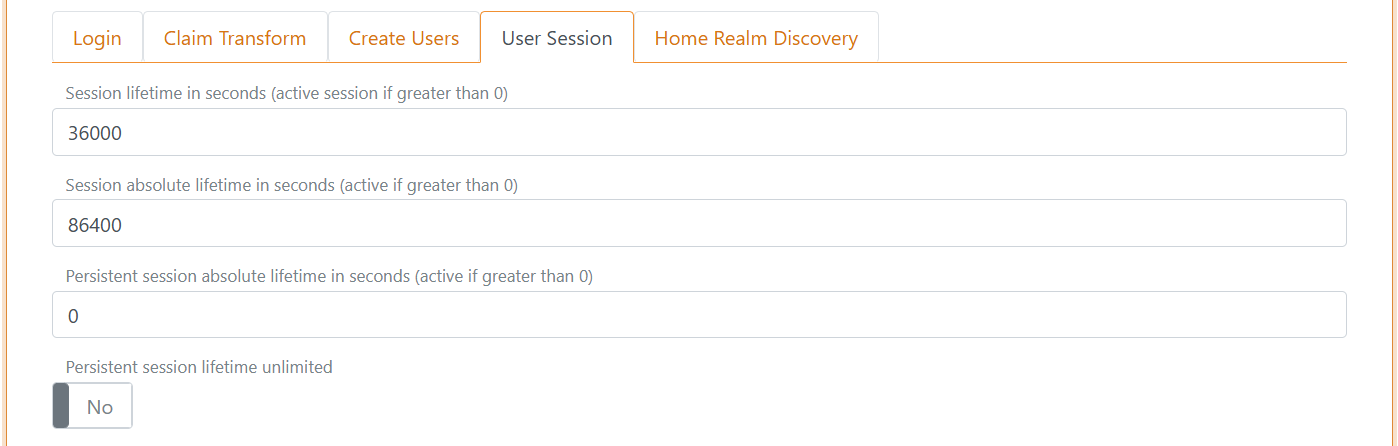
Click Show advanced to change the user sessions lifetime. The default lifetime is 10 hours.
The user session is a sliding session, where the lifetime is extended every time, an application makes a login request until the absolute session lifetime is reached.
It is possible to configure an absolute session lifetime or not.
The user session can be changed to a persistent session which is preserved when the browser is closed and reopened.
The user session become a persistent session if either the persistent session lifetime is configured to be grater, then 0. Or the persistent session lifetime unlimited setting is set to Yes.
Click the
User sessiontag to see all session settings.
Configure claims
You can change the claims and do claim tasks with claim transforms and claim tasks.
