Users
Users are saved in the environment's user repository. To achieve multiple user stores, you create additional environments and thus achieve more user stores.
There are two different types of users:
- Internal users which are authenticated using the login authentication method.
- External users which are linked by an authentication method to an external user/identity with a claim. The users are authenticated in an external Identity Provider and can be redeemed based on e.g. an
emailclaim (see Provision and redeem section in external users doc).
Another option is to authenticate against an existing external user store via an API. In this case the users are not saved as internal users in the environment. The users can optionally be created as external users.
Failing login lockout
If a user fails to log in and enters a wrong password a number of times within a given lockout count period, the user is locked for a period of time (observation period) and is automatically unlocked once the period ends.
Lockout is enforced for user authentications using the login and external login authentication methods.
This is a security feature to prevent brute force attacks on user accounts. It is not recommended to disable this feature, but you can configure the lockout count, lockout period and count timeframe to suit your needs.
The lockout is configured in the environment settings in the FoxIDs Control Client.
- Select the Settings tab
- And subsequently select the Environment tab
- Find the Failing login lockout section
- Set the Lockout count timeframe to the number of allowed failed login attempts, e.g.
5for 5 attempts - Set the Lockout period in seconds, e.g.
36000for 10 hours - Set the Count time period in seconds, e.g.
3600for 60 minutes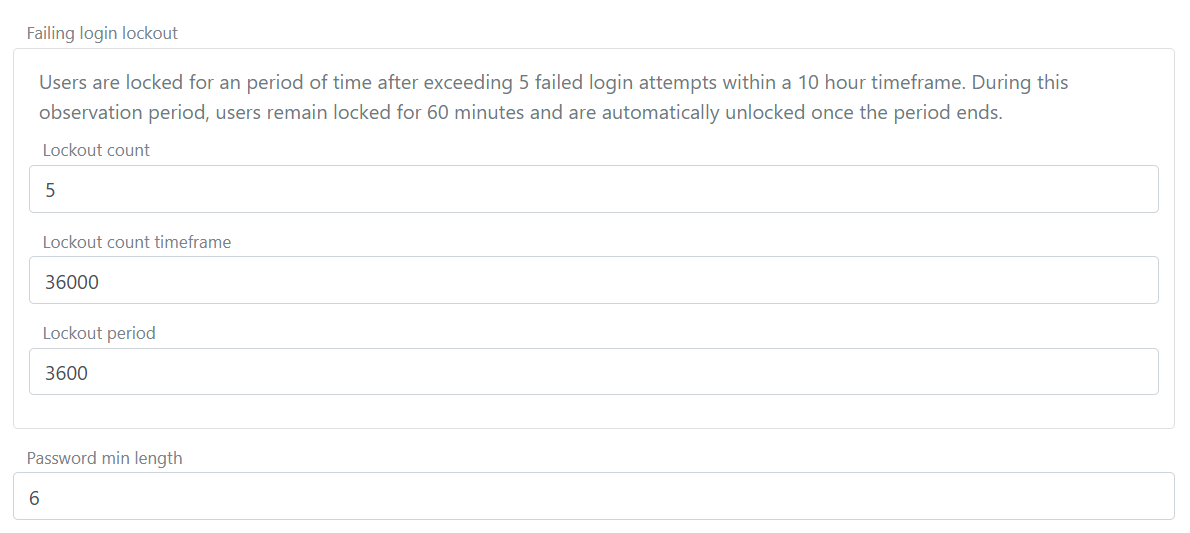
- Click Update