SAML 2.0 authentication method
FoxIDs SAML 2.0 authentication method which trust an external SAML 2.0 Identity Provider (IdP).
SAML (Security Assertion Markup Language) 2.0 is an open standard for exchanging authentication and authorization data between
an Identity Provider (IdP) and a Service Provider (SP). It enables Single Sign-On (SSO), allowing users to log in once and gain access to multiple applications without needing to authenticate again.
The two SAML 2.0 flows are supported. The SP-Initiated Login flow, which is the default, most common and recommended flow, and the IdP-initiated Login flow.
SAML 2.0 is widely used in enterprise environments, enabling secure identity federation across different organizations and applications.
By configuring an SAML 2.0 authentication method and a OpenID Connect application registration FoxIDs become a bridge between SAML 2.0 and OpenID Connect. FoxIDs will then handle the SAML 2.0 connection as a Relying Party (RP) / Service Provider (SP) and you only need to care about OpenID Connect in your application.
It is possible to configure multiple SAML 2.0 authentication methods which can then be selected by OpenID Connect application registrations and SAML 2.0 application registrations.
Configure IdP-Initiated Login and forward the login to SAML 2.0 and OpenID Connect applications.
FoxIDs support SAMl 2.0 redirect and post bindings. Both the login, logout and single logout SAML 2.0 profiles are supported. The Artifact profile is not supported.
An authentication method expose SAML 2.0 metadata and can be configured with SAML 2.0 metadata or by manually adding the configuration details.
The FoxIDs generated SAML 2.0 metadata only contain logout and single logout information if logout is configured in the SAML 2.0 authentication method.
FoxIDs support all SAML 2.0 identity providers (IdPs) and has been tested against a wide range of IdPs.
How to guides:
- Connect PingIdentity / PingOne
- Connect Google Workspace
- Connect Microsoft AD FS
- Connect NemLog-in (Danish IdP)
- Connect Context Handler (Danish identity broker)
- Connect two FoxIDs environments in the same tenant with a Environment Link
Configuration
How to configure an external SAML 2.0 Identity Provider (IdP).
The FoxIDs SAML 2.0 authentication method metadata endpoint is
https://foxids.com/tenant-x/environment-y/(some_external_idp)/saml/spmetadata. If the IdP is configured in tenanttenant-xand environmentenvironment-ywith the authentication method namesome_external_idp.
The following screenshot shows the configuration of a SAML 2.0 authentication method in FoxIDs Control Client.
Here the configuration is created with the external IdPs metadata. The forwarded claims is limited to the configured set of claims, default all claims is forwarded with the * notation.
More configuration options become available by clicking Show advanced.
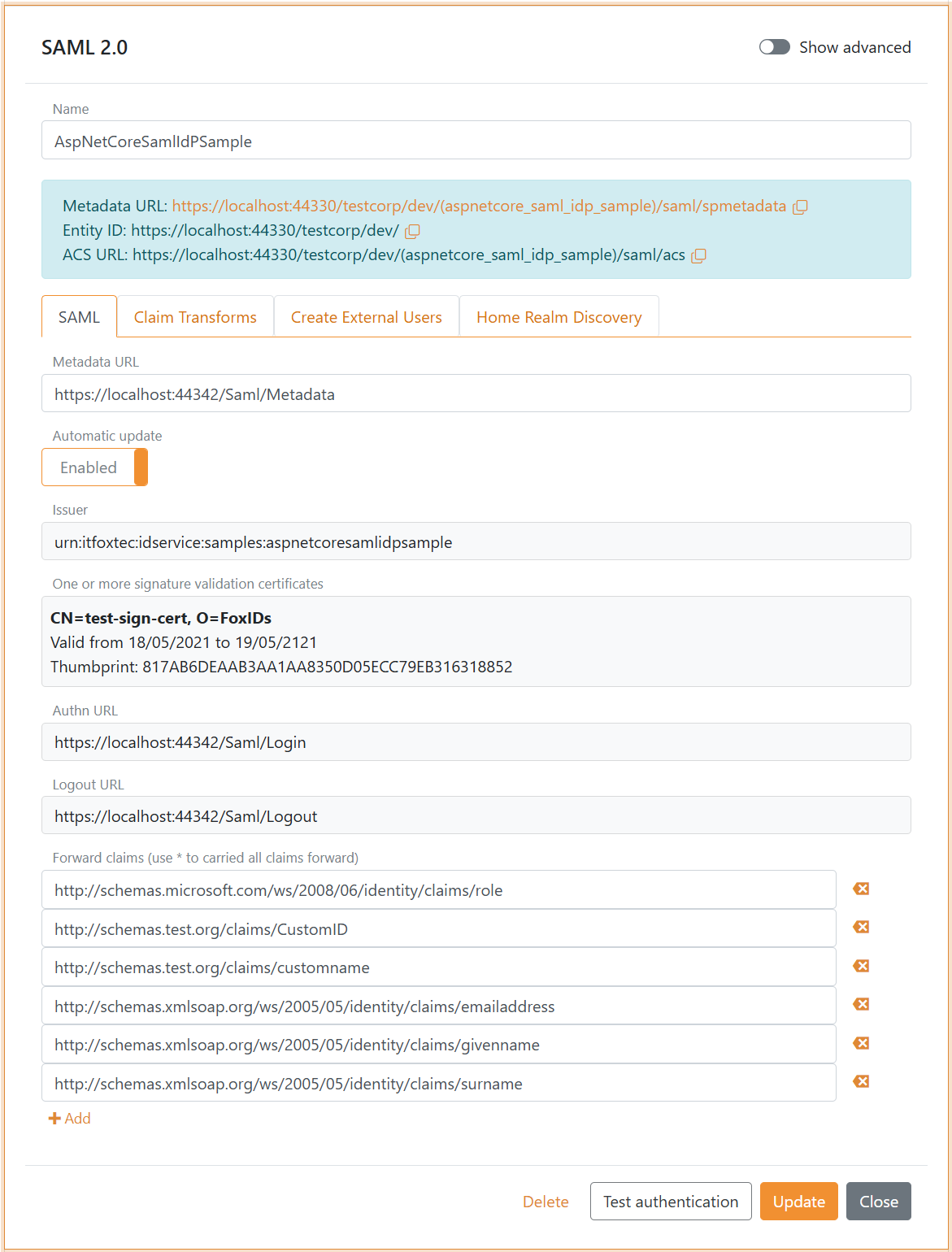
You can change the claims and do claim tasks with claim transforms and claim tasks.
Manual configuration become available by disabling Automatic update. This way the IdP do not need to expose or send a metadata file, you can configure it all manually.
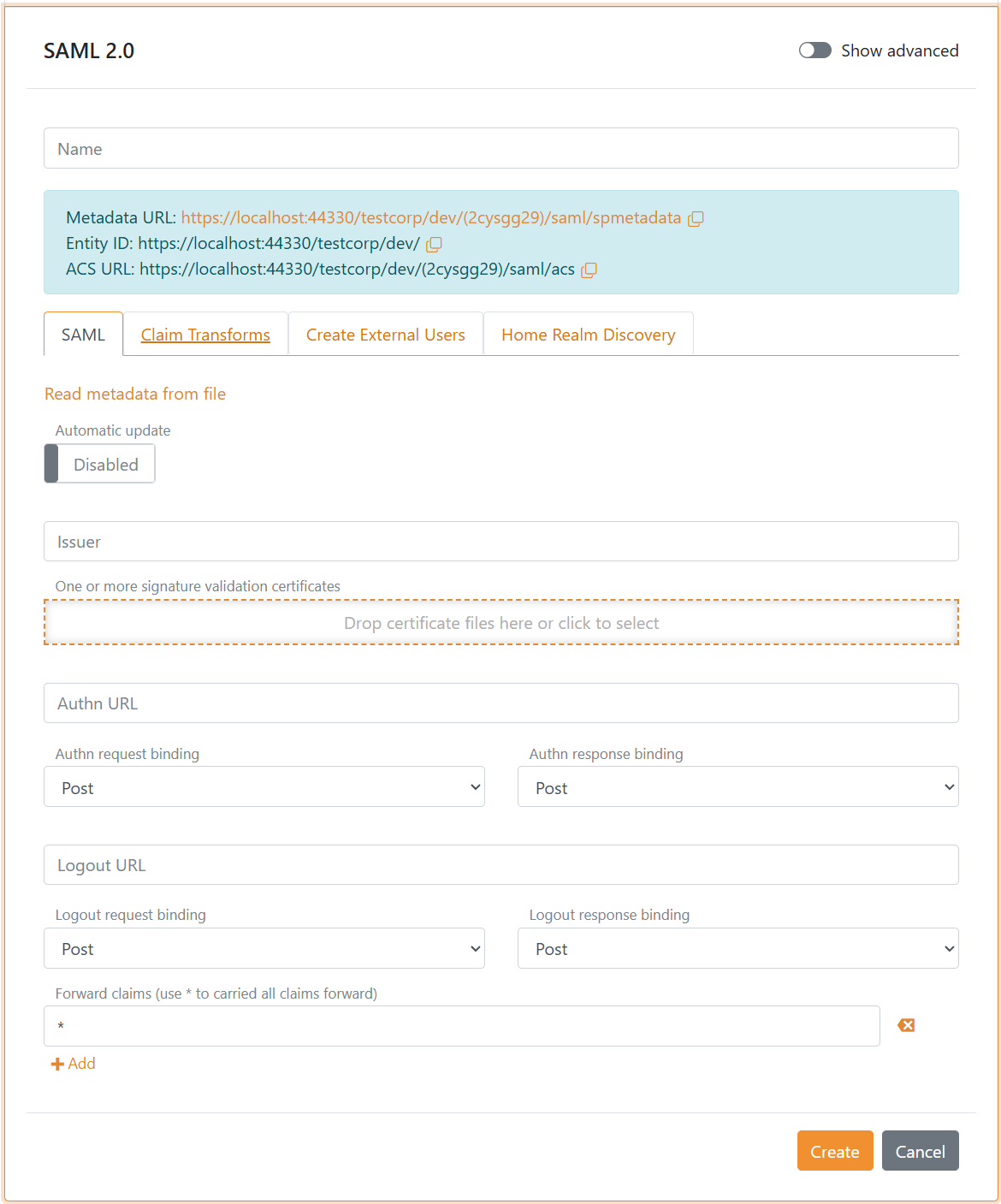
If you are creating a new claim, add the claim or * (default) to the Forward claims list to forward the claim to the application registration.
IdP-Initiated Login
SAML 2.0 IdP-Initiated Login is a Single Sign-On (SSO) authentication flow where the process starts at the Identity Provider (IdP) instead of the Service Provider (SP). This method is commonly used in enterprise environments to allow users to access multiple applications with a single authentication.
Unlike SP-Initiated Login, the SP does not request authentication from the IdP. The IdP sends the an unsolicited SAML assertion on its own initiative. This key different makes the IdP-Initiated Login flow less secure then the SP-Initiated Login flow, and for this reason IdP-Initiated Login is disabled by default in FoxIDs.
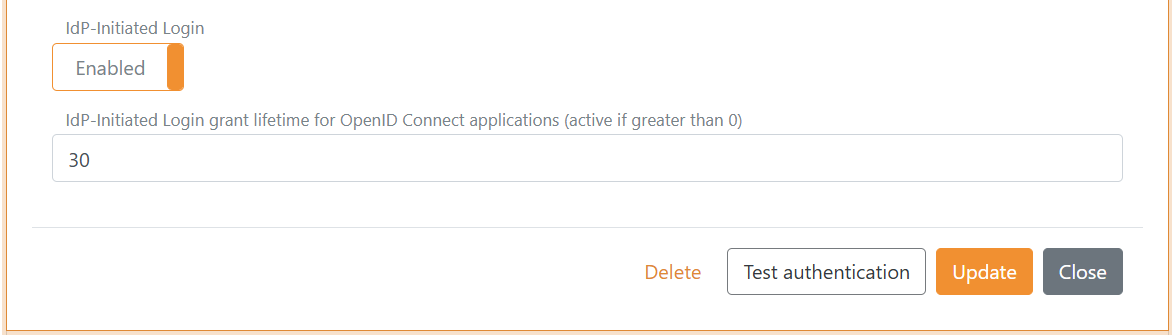
Enable IdP-Initiated Login.
- Open the SAML 2.0 authentication method in FoxIDs Control Client
- Click Show advanced
- Scroll to the bottom of the configuration section
- Enable IdP-Initiated login
- Optionally change the IdP-Initiated Login grant lifetime for OpenID Connect applications
- Click Update
The configure the SAML 2.0 authentication method to trust the IdP in the same way as if you were to use SP-initiated login.
IdP Relay State
The external IdP must send a relay status that specifies the application to which the authentication should be forwarded.
The relay status must always contain the application name app_name and application type app_type and in some cases must contain an application redirect URL app_redirect.
The elements has each a name and a value and they are decided by &. The redirect URL values must be URL encoded. The application type value can either be saml2 or oidc.
The SAML 2.0 identity provider (IdP) .NET sample AspNetCoreSamlIdPSample show how to create a IdP-Initiated Login with a relay state.
SAML 2.0 application
If you want to foreword the authentication to the SAML 2.0 application named my-saml2-app, the relay state is:
app_name=my-saml2-app&app_type=saml2
This will foreword the authentication call to the first Assertion Consumer Service (ACS) endpoint configured for the application.
If you want to foreword the authentication to another configured ACS endpoint https://my-domain.com/auth/acs2, the relay state is:
app_name=my-saml2-app&app_type=saml2&app_redirect=https%3A%2F%2Fmy-domain.com%2Fauth%2Facs2
The authentication call is foreword to the SAML 2.0 application as an IdP-Initiated Login with an unsolicited SAML 2.0 authn response.
OpenID Connect application
OpenID Connect does not support IdP-Initiated Login. Therefor, the IdP-Initiated Login is verified in the authentication method and forwarded to the OpenID Connect application by
calling the application with redirect URL app_redirect which should start the login flow (OpenID Connect standard: Initiating Login from a Third Party).
You need a page in the OpenID Connect application that requires the user to be authenticated and therefore starts the login flow when called.
A issuer iss parameter is passed along in the query that you can choose to validate.
The OpenID Connect application can make a general login request with an *, FoxIDs know where to route the login request.
Then the OpenID Connect application calls FoxIDs, which read the IdP-Initiated Login grant.
Alternatively, without an IdP-Initiated Login grant the external IdP is called with an SP-Initiated Login flow.
The external IdP uses the Single Sign-On (SSO) context and replies to FoxIDs.
It is recommended to use the IdP-Initiated Login grant functionality to avoid an extra round-trip to the external IdP.
The SAML 2.0 IdP-Initiated Login is then translated to OpenID Connect and forewords the authentication to the OpenID Connect application.
If you want to foreword the authentication to the OpenID Connect application named my-oidc-app with the login initiating URL https://my-domain.com/secure-page,
the relay state is:
app_name=my-oidc-app&app_type=oidc&app_redirect=https%3A%2F%2Fmy-domain.com%2Fsecure-page
The application redirect URL must be a valid/configured URL for the OpenID Connect application.

