Connect to NemLog-in with SAML 2.0 (Template)
Use the NemLog-in template to configure a SAML 2.0 authentication method with OIOSAML 3.0.3 defaults. The template guides you through the public or private sector setup and generates the metadata you upload to NemLog-in.
This guide covers OIOSAML 3.0.3 only. OIOSAML 4.0.0 is not covered at this time.
Pricing
NemLog-in for private sector is a low-cost way to offer MitID login. NemLog-in adds 0.02 DKK on top of the MitID base price (which applies to all brokers) and NemLog-in has no monthly fee. The tradeoff is that NemLog-in uses SAML 2.0 (OIOSAML) and has additional requirements. FoxIDs handles this and lets you connect your application with OpenID Connect.
| Item | Price |
|---|---|
| One-time NemLog-in onboarding fee | 4,500 DKK |
| NemLog-in price per login | 0.02 DKK |
| MitID base price per login (applies to all MitID brokers) | 0.175 DKK |
| Total price per login | 0.195 DKK |
| FoxIDs Pro plan per month (includes 2,000 logins per month) | 223.80 DKK |
| FoxIDs price per login | 0.038 DKK |
The same price applies for both MitID private users and MitID employee users.
NemLog-in is free to use for the public sector.
OpenID Connect bridge
By configuring a SAML 2.0 authentication method and an OpenID Connect application registration FoxIDs becomes a bridge between SAML 2.0 and OpenID Connect. FoxIDs then handles the SAML 2.0 connection as a Relying Party (RP) / Service Provider (SP) and you only need to care about OpenID Connect in your application.
Get started with NemLog-in
Before you can create IT systems for NemLog-in, your organization must be connected. This is only necessary once per organization.
- Follow the NemLog-in onboarding steps at https://tu.nemlog-in.dk/tilslutning/ (one-time per organization)
- Once the organization is connected, create IT systems in the NemLog-in administration portal. Each IT system integration test or production tab corresponds to a FoxIDs authentication method.
Other useful resources:
- The NemLog-in development portal with documentation for test and production environments
- Test user creation in the MitID emulator and MitID simulator
- Integration with NemLog-in (PDF) with a detailed description of the integration flow (secondary reading)
Consider a separate environment
NemLog-in requires an OCES3 certificate and extended logging. The template updates the environment configuration accordingly, so consider creating a separate environment dedicated to NemLog-in.
You can connect two environments in the same tenant with an Environment Link.
Create the NemLog-in authentication method (template)
Start by configuring a NemLog-in integration test connection and then the production connection.
1) Start in FoxIDs Control Client
- Go to the Authentication tab
- Click New authentication
- Select NemLog-in - SAML 2.0
2) Configure the template
- Enter a name for the authentication method
- Select Sector:
- Public sector (OIOSAML 3.0.3)
- Private sector (OIOSAML 3.0.3)
- Select NemLog-in environment:
- Integration test
- Production
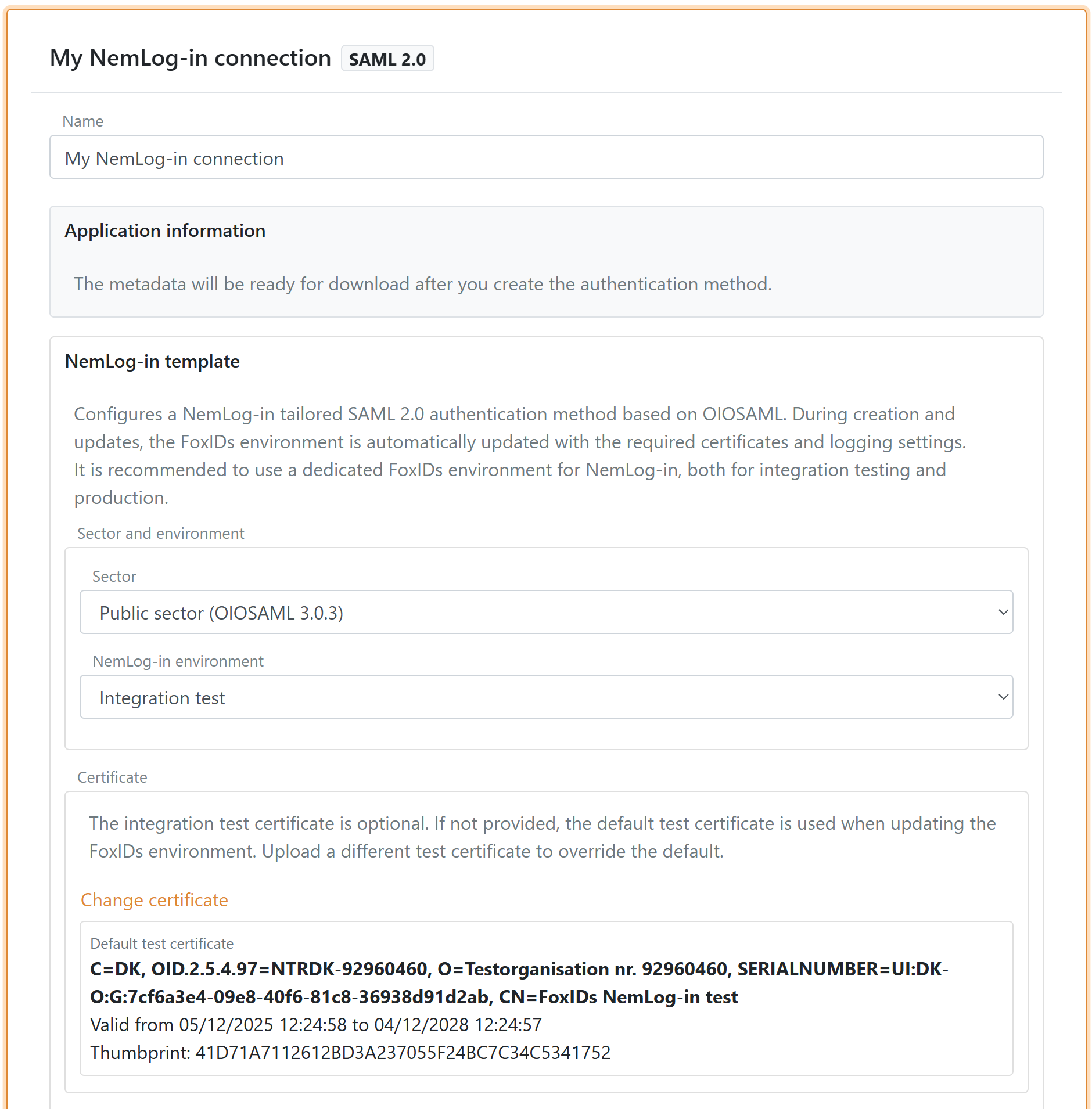
3) Private sector CPR flow
If you select the private sector, you can enable (default enabled):
- Request CPR to ask the user for a CPR number during login
- Save CPR on external users to store CPR on the external user so the user only needs to enter CPR once or you can set a lifetime for the saved CPR on the external user
The template configures the CPR match UI flow automatically.
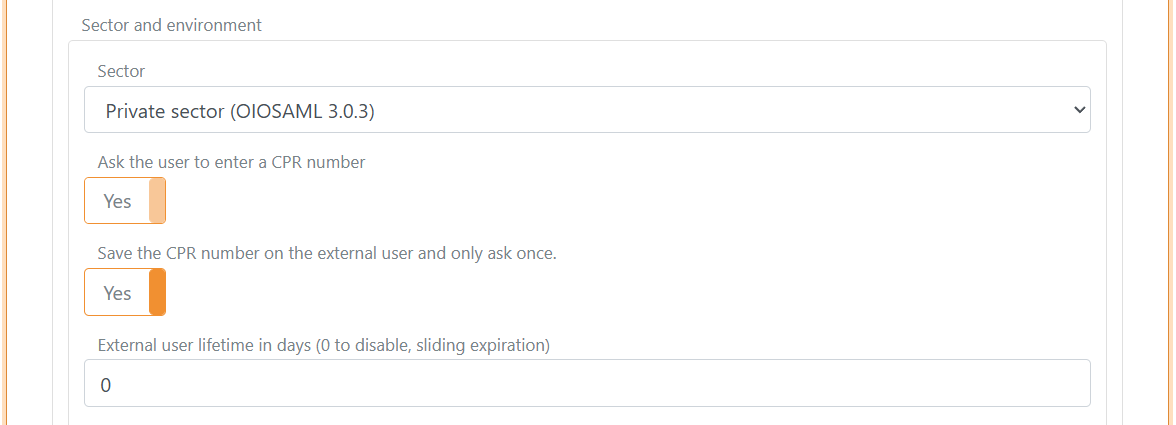
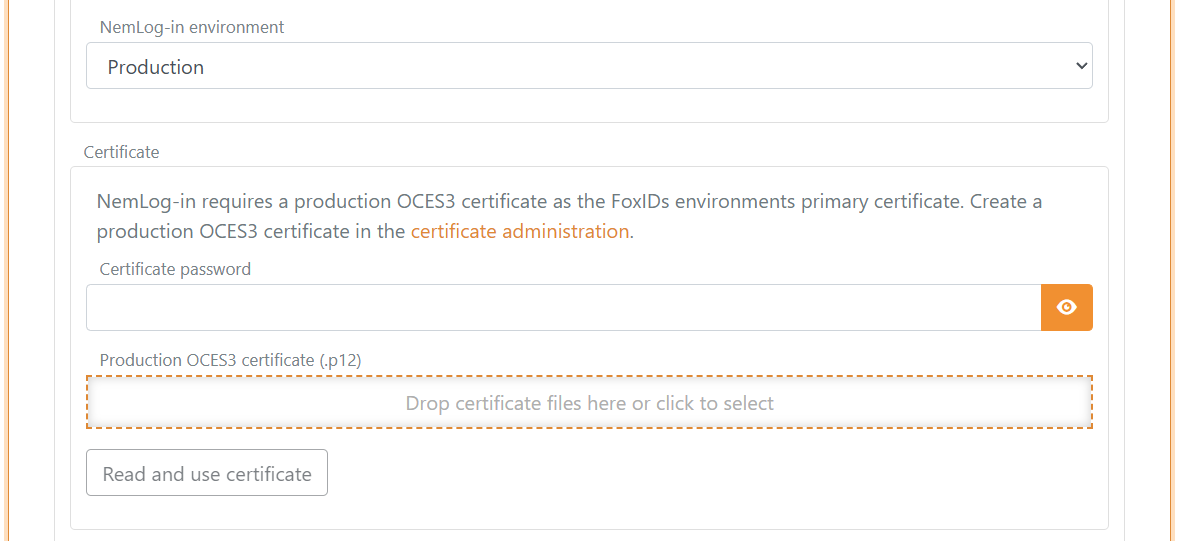
4) Configure certificate
NemLog-in requires an OCES3 certificate.
- Integration test: the template can use a default test certificate, which you can replace if needed
- Production: upload your own OCES3 certificate. You can create a production OCES3 certificate in the certificate administration
An OCES3 certificate is valid for 3 years. Update the NemLog-in template before the certificate expires and update the certificate in NemLog-in.
5) Metadata URL and IdP metadata
The template pre-fills the NemLog-in IdP metadata URL for the selected environment.
When NemLog-in changes certificate, the change is provisioned automatically. The NemLog-in template uses NemLog-in metadata exposed via the FoxIDs website, which we keep updated, and the template automatically loads the new metadata.
6) Level of assurance (optional)
You can optionally set a minimum level of assurance (LoA) (OIOSAML 3.0.3):
- Low
https://data.gov.dk/concept/core/nsis/loa/Low - Substantial
https://data.gov.dk/concept/core/nsis/loa/Substantial - High
https://data.gov.dk/concept/core/nsis/loa/High
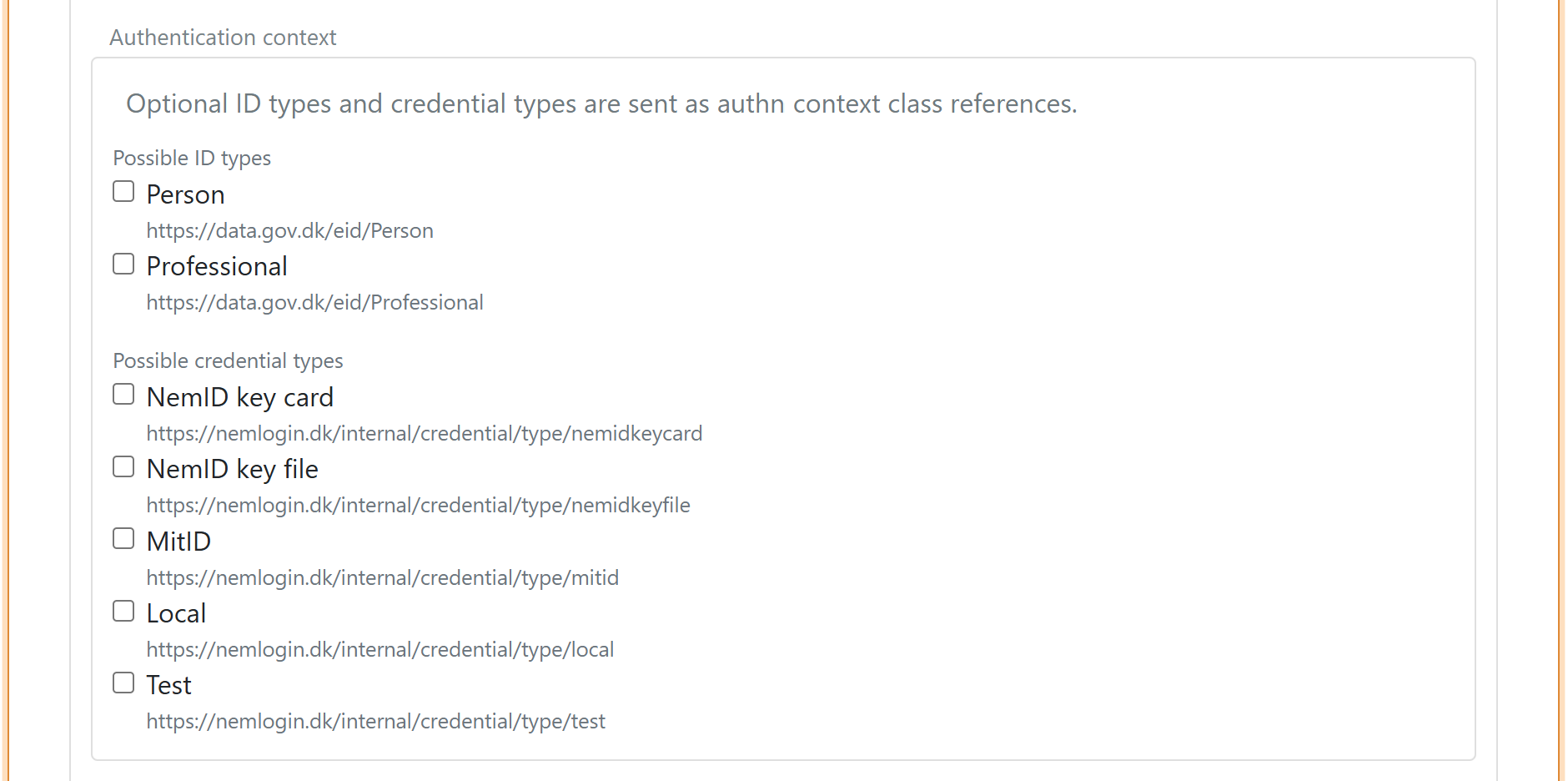
7) Authentication context (optional)
You can optionally set authentication context requirements.
You can specify ID type:
https://data.gov.dk/eid/Personhttps://data.gov.dk/eid/Professional
And possible credential types:
https://nemlogin.dk/internal/credential/type/nemidkeycardhttps://nemlogin.dk/internal/credential/type/nemidkeyfilehttps://nemlogin.dk/internal/credential/type/mitidhttps://nemlogin.dk/internal/credential/type/localhttps://nemlogin.dk/internal/credential/type/test
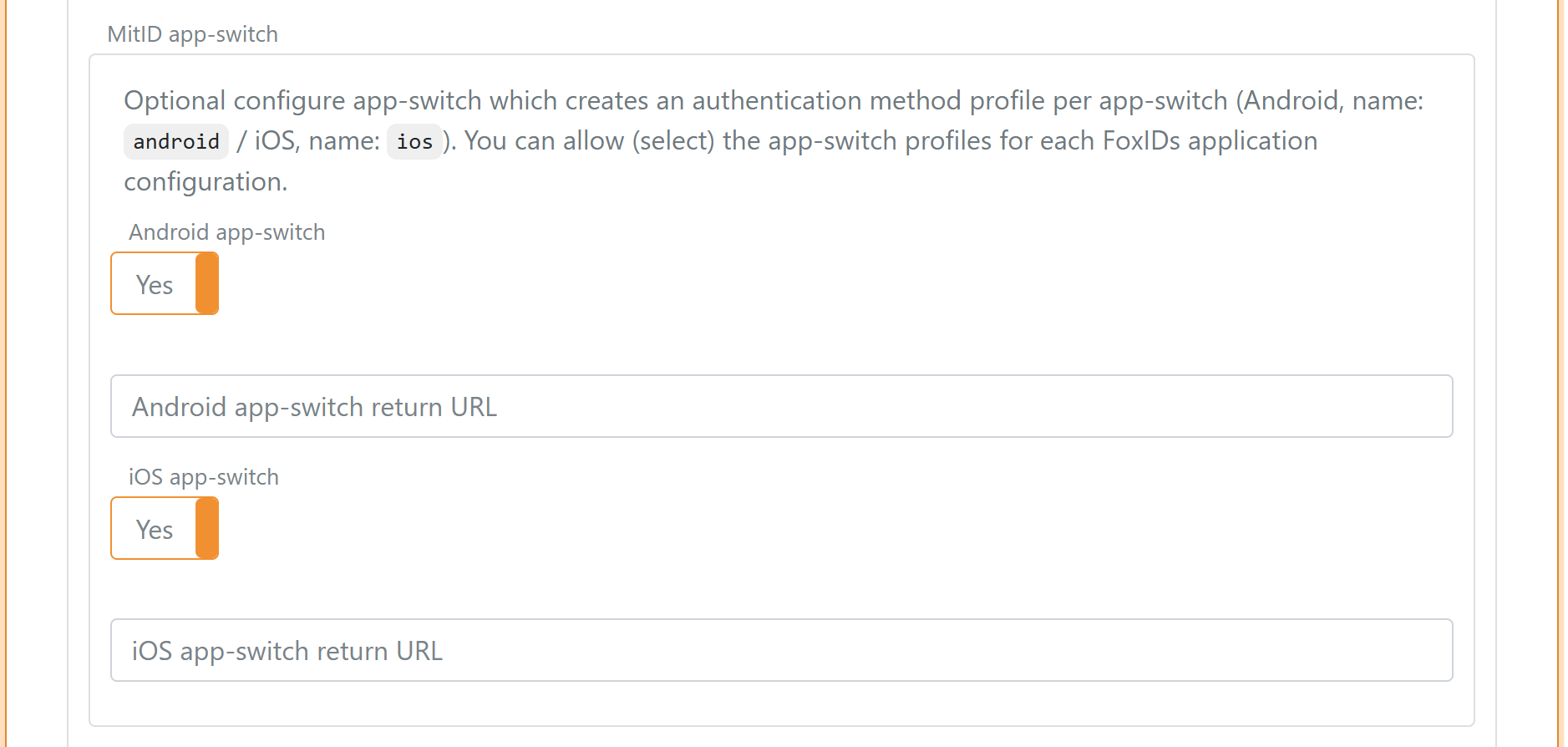
8) App-switch
Optionally configure app-switch to create one authentication method profile per mobile platform. You can then allow (select) the profiles per FoxIDs application configuration.
- Android profile name:
android - iOS profile name:
ios
Further reading:
- Integration of mobile applications with NemLog-in
- Integration with NemLog-in (PDF) (see chapter "12.8 Mobile app-switch")
9) Add contact person
Add at least one technical or administrative contact person in metadata.

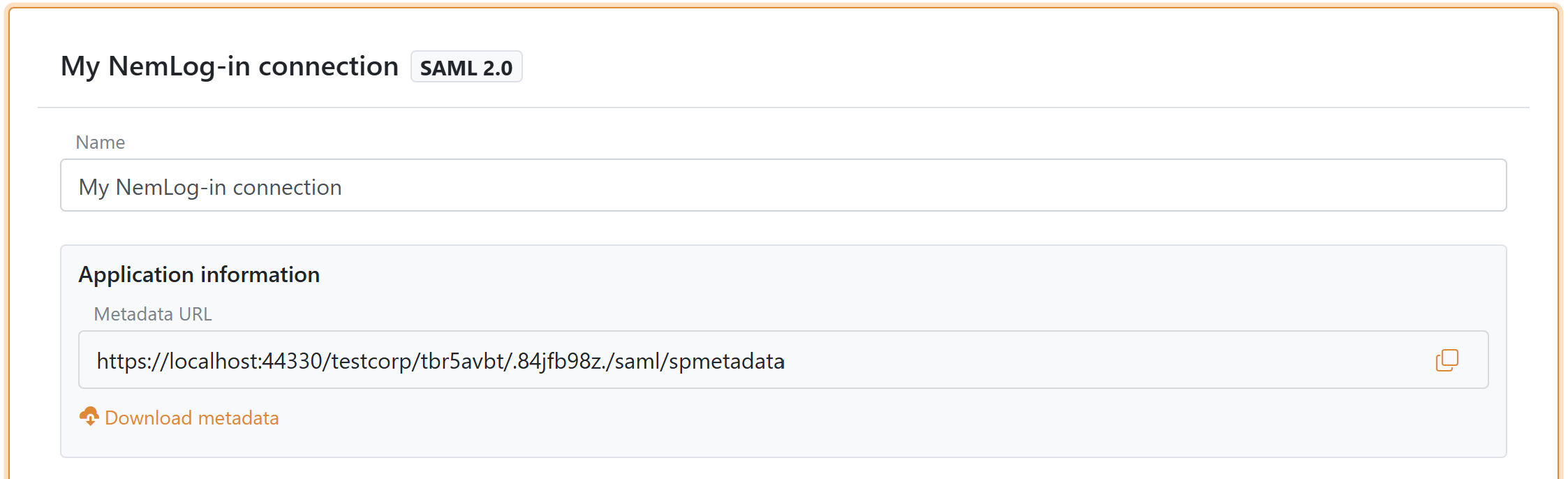
10) Create and download SP metadata
Click Create or Update. After the authentication method is created, the Application information section shows the metadata URL and a download button (in the top of the NemLog-in template).
If you change attributes or authentication context later, you must upload the metadata again in NemLog-in.
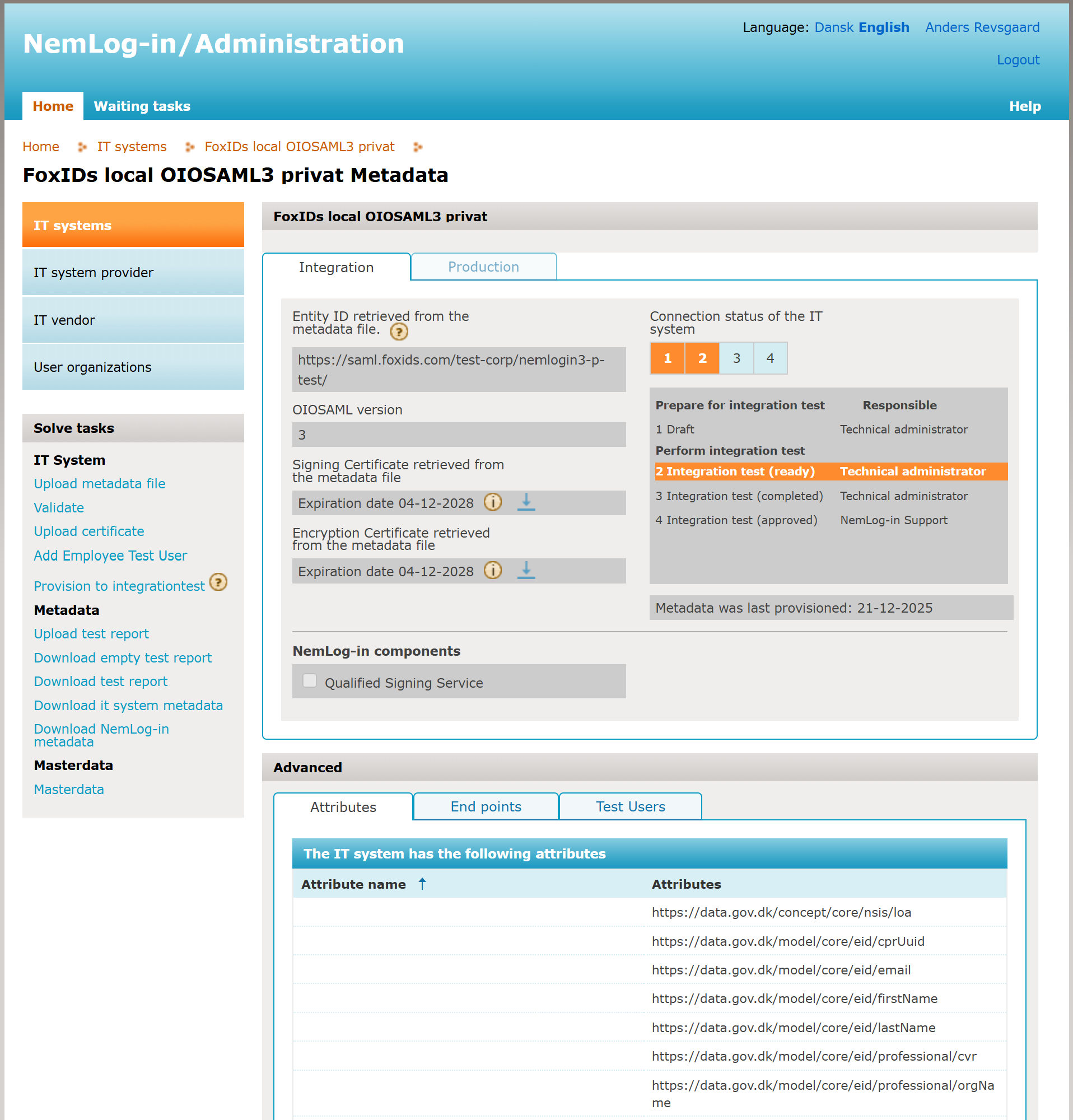
Configure the NemLog-in IT system
When you create an IT system in NemLog-in it has two tabs: integration test and production.
- Create a FoxIDs NemLog-in connection for integration test with the template
- In the NemLog-in administration portal, upload the SP metadata to the integration test tab and provision to integration test
- Upload the test report:
- After approval, the production tab opens
- Create a FoxIDs NemLog-in connection for production with the template
- Upload the SP metadata to the production tab and provision to production
- You are now in production with MitID
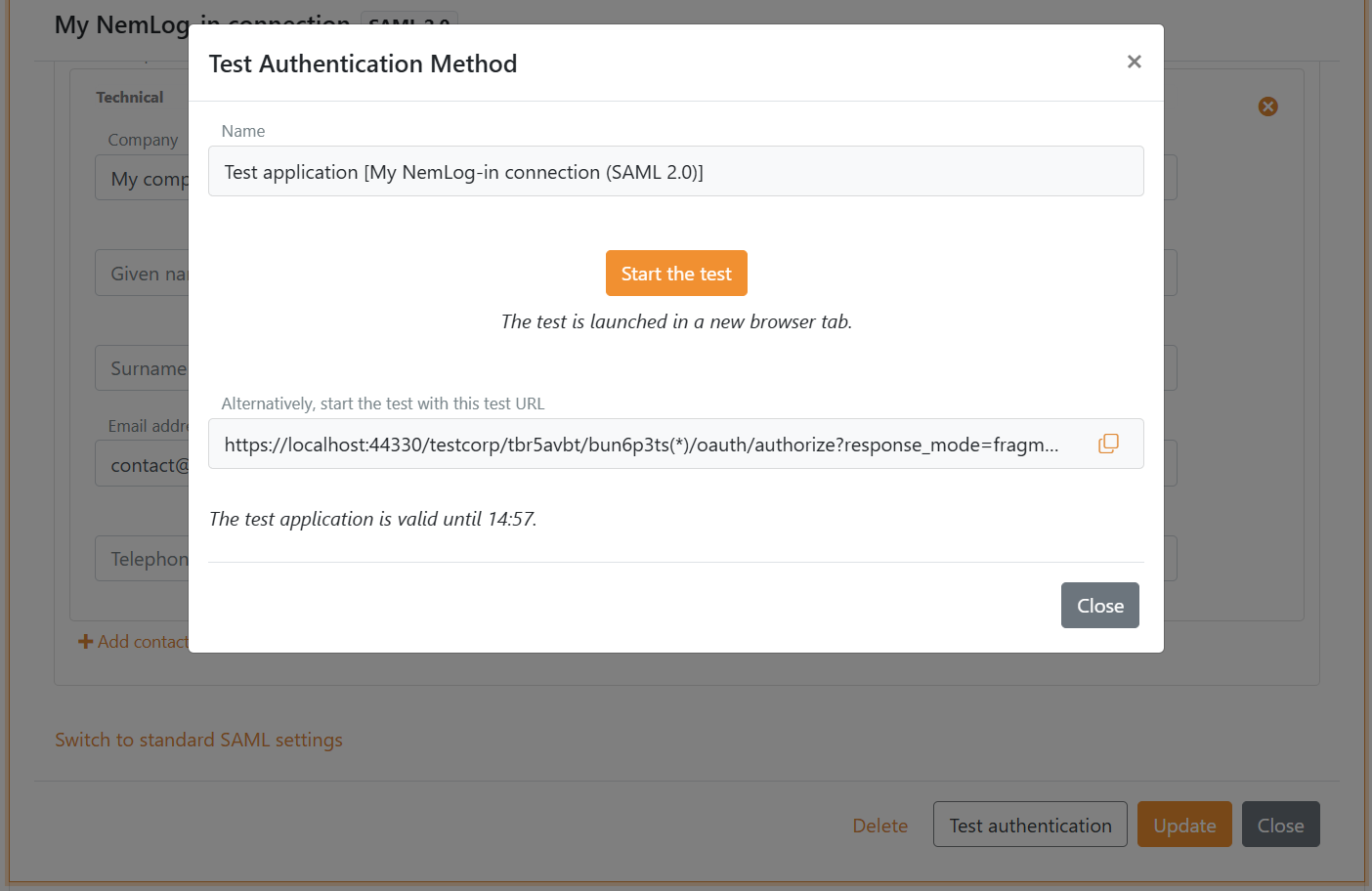
Test the authentication method
- Go back to FoxIDs Control Client and open the NemLog-in authentication method
- Click Test authentication to create a test application
- Click Start the test to start the test
Legacy
If you need the legacy guide for configuring NemLog-in with the standard SAML 2.0 settings, see Connect to NemLog-in with SAML 2.0 (Legacy standard configuration).
